Since we already had a database of user accounts, we naturally turned to a centralized authentication system. This is how we introduced SSO.
Single sign-on, also known as SSO, is a centralized authentication method designed to authenticate a user only once to access a wide range of apps for which the user account is authorized.
SSO set-up
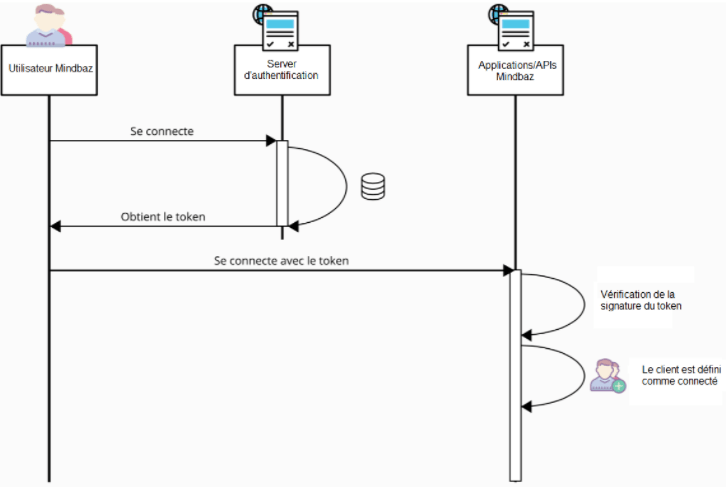
The move to a centralized authentication system requires implementing an authentication server, which acts as a centralized directory to control user access to different resources.
The server issues an authentication token, also known as a JWT (Json Web Token). This token is then sent to the client and, with each HTTP request to the server, enables it to identify the user.
At Mindbaz, we’ve also set up an authentication app, linked to the SSO server:
- Login/password authentication
- Lost password
- Password reset
- Account unlocking
This allows us to centralize authentication rules such as password definition and activities on the user account.
How single sign-on or SSO works
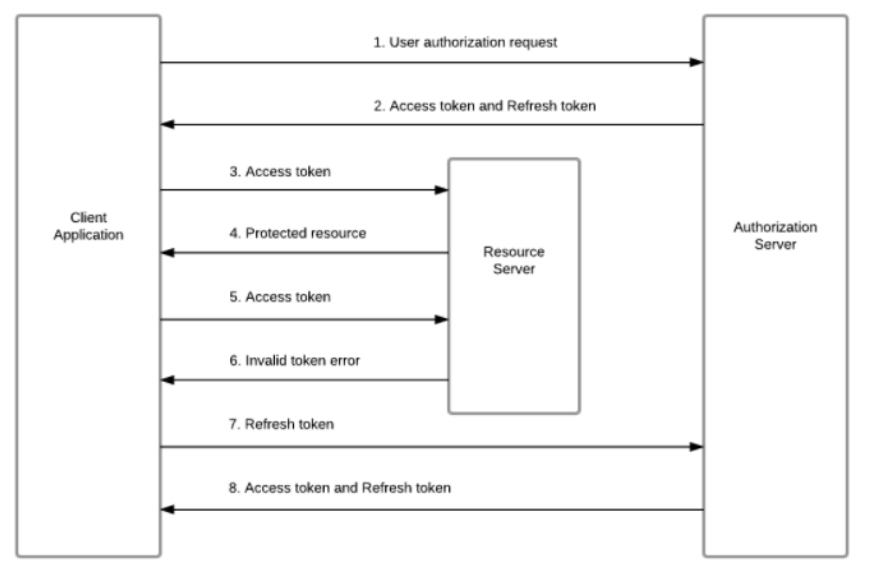
When the server receives a JWT token from a client request (API or app), it is validated using the information stored in its payload. This payload contains the exact time when the token was issued, thus making it possible to check if it is still valid.
The token’s validity period is one of the parameters set by the authentication server when the token is issued.
If the token expires, its payload contains data called “refresh token”. When a resource is called (website/API) and the token is identified as expired, sending the refresh token data to the SSO enables the client app to extend the token’s validity by requesting the issue of a new token/refresh_token pair. When the token is extended, SSO re-validates the user’s access and issues a new token/refresh_token pair, while also disabling the previously issued pairs.
The user is thus transparently “re-connected” to the resource they wanted to access.
Issues and concerns of SSO
Since tokens give access to a wide range of potential resources, depending on the rights granted to the user, if an account is stolen, a hacker could gain access to much more data and applications than with a unique account for each app. Therefore, security measures to reinforce authentication go hand in hand with using SSO.
At Mindbaz, we have also implemented dual authentication to reinforce this. When a new login is made from an unknown location, an e-mail is sent to the user, and a one-time text message code is required to confirm the login.
Oauth2
SSO is based on a number of protocols, especially the Oauth2 protocol, which defines technical specifications for the use of this type of authentication.
This protocol is widely used by websites such as Google and Facebook, and has become an industry standard.
